Secure Communication in unsecure networks
 Is GSM communication secure against Tapping?
Is GSM communication secure against Tapping?
In all areas of Business, communication by mobile phone has become a necessity in order to react fast to customers’ needs. Users exchange confidential and sensitive data about their business via public networks unaware of how this information is handled. Users believe that their information is kept confidential and protected against interception. This trust is a dangerous misapprehension and misperception. There are a lot well documented attack methods against the GSM standard and its security functions. Not only on laboratory level or on network- operator level but also on practical level with passive, fully transparent and undetectable monitoring devices.
Who is tapped?
The damage caused by industrial spying in Germany is estimated at 30 billion € / per year. In the meantime many companies pay attention for the security dangers for their EDP - systems. But they are not aware to the risks and threats of manipulation and monitoring their language communication with its high potential of danger. In particular, large corporations doing international business such as investment bankers and innovative medium-sized companies in highly competitive international markets are at risk. But the estimated number of unknown cases of undiscovered eavesdropping activity is much more higher. In particular, for medium-sized businesses in the context of the competitive area of tenders and the subsequent contractual negotiations that follows. Suspicions are frequently raised that quotations and negotiation positions have been revealed by eavesdropping either by or on behalf of competitors. Little criminal energy is needed to reach this information by intercepting all mobile communications in a small radius around the location where the tenders are received and the negotiations take place. Secretly, all phone calls made by the competitor will have been intercepted
.
What can be done?
Use the “tap-proof“ mobile TMPSYS- T 301E Enigma encryption solution for all your sensitive communications.
Technical Data Security
Overview Security Module Features
Encryption algorithm: AES-256bit
Authentication algorithm &
key exchange: RSA 1024 bit/ RSA 2048 bit
Authorization algorithms: BlackList/ WhiteList /CUGList
Hash algorithms: RIPEMD-160/SHA256
Digital Certificates: X509v3
Transportation data formats: CSD, V110
Crypto Cards: Deutsche Telekom/ T-Systems Int. GmbH
Netkey Cards: ITSEC Certification Level 4, mech. strength HIGH.
Encryption Services: Speech & SMS
Option: Customer Key management
 The TMPSYS-Enigma Mobile Phone
The TMPSYS-Enigma Mobile Phone
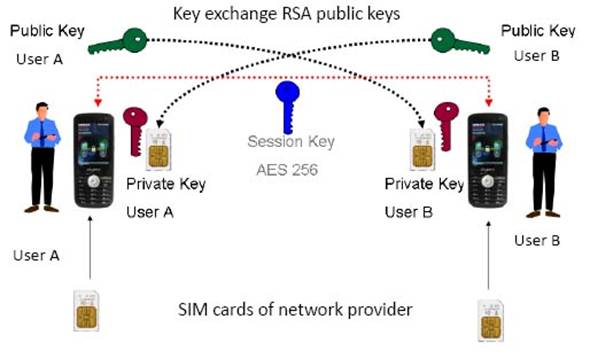
Interception-proof by Means of a Two-step Encryption Method
Each TMPSYS-Enigma works with an individually generated and certified key pair of the Trust Centre. These are stored on the net key card which is inserted into the phone. If another TMPSYS-Enigma (which has its own individual key pair) is called using the crypto functionality, the partners are authenticated by means of the certificates of the two chip cards. A —one time pass session key (one out of 10^ 77 possible keys) is generated and exchanged between the parties encrypted by the keys of the Crypto cards. The session key itself encrypts all communication data transmitted between the two phones. Whoever intercepts this encrypted data stream will only hear a noise which cannot be decrypted even with the highest performance mainframe computers.
TMPSYS- T 301E Enigma - A High Performance GSM Phone even for “Normal“ Calls
TMPSYS-Enigma will operate efficiently in all standard 900/1800/1900 GSM networks. In addition to the integrated encryption system TMPSYS-Enigma has all the features of a normal, modern business mobile phone. It can be used for normal unencrypted calls to any other phone. For all encrypted (secure) communications as well as for all unprotected calls your standard SIM card is used meaning that you do not have to change your phone number to use TMPSYS-Enigma to it‘s maximum. GSM SIM Card subscription must include circuit switched data services (CSD) under all roaming conditions.
In spite of the serious background relevant for security the TMPSYS-Enigma T 301E mobile phone with its extensive business functions is a practical and perfect partner for everyday life usage.
TMPSYS-Enigma T301E with encrypted SMS feature.
Crypto-SMS uses the same encryption algorithms as the encrypted speech service. User Groups can be organized simple by exchanging their certificates of the security card.
Technical Data
Strong hybrid End – to End - Encryption over GSM Data Channel ( CSD )
2,4" TFT Display
3.0 MP CMOS Camera
Micro SD Card up to 2 GB
USB 1.1
WAP 2..0
Enhanced SMS / MMS
Multimedia and Organizer
Unified Message Box
92,5 gr. Weight
GPRS Class 12
Tri Band GSM 900 ,GSM 1800 and PCS 1900
Battery Lithium-Ion 950 mAh
Bluetooth (only for clear calls)
Talk Time : up to 7 hours.
Standby : 450 to 600 hours.
FM radio
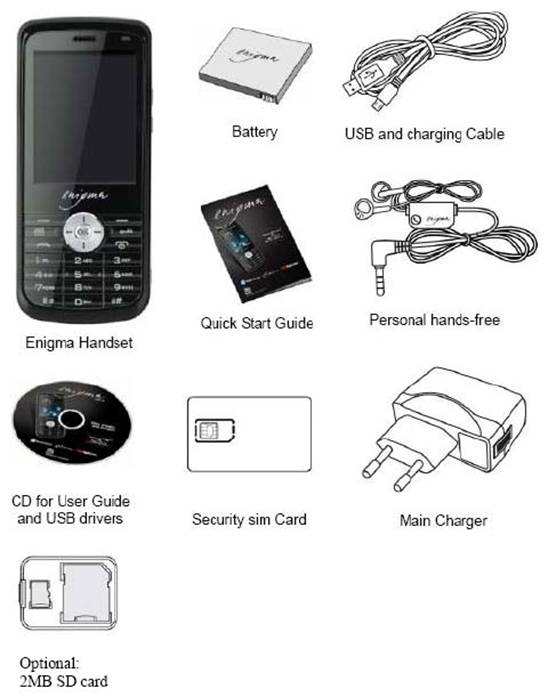
Standard Package :
TMPSYS-T301E, Main Charger, Personal hands-free , USB-Cable, 2 GB Micro SD Card, Manual
Encryption
The TMPSYS-Enigma T301E provides a worldwide unique, actual, user-friendly and efficient end- to- end encryption GSM solution for safe mobile language communication in unsecure GSM networks. It is dedicated to highly demanding users: to business as well as to public administration, police and army. The TMPSYS-Enigma T301E guarantees extremely reliable cryptography combined with excellent voice quality.
Hybrid Encryption method
Encryption Features
- Strong hybrid End – to End - Encryption
- TMPSYS-Enigma T301E is based on a Mediatek solution comprising three core processors on the GSM part
- The complete Crypto part is running on a separate Crypto board independent of the GSM part to avoid tapping
- Pre-compression speech encoding for superior speech quality.
- Well established Open protocol Encryption Standards employed, RSA, AES, RIPEMD-160/SHA 256 bit *1)
- User Authentication by asymmetric RSA 1024 bits/2048 bit, X509 v3 certificates (located inside the smart card ).
- Smart Card issued by either Infineon or Phillips
- Digital Signatures according to strict German Digital Signature Act, SigG.
- Using TeleSec Netkey Cards as highly secure Crypto cards
- Security Cards (Netkey)Certified to ITSEC (*2) Evaluation level E4, mechanical strength HIGH.
- Alternative TCOS min 3.0 Cards with customer generated keys and own administration (CA Management tool required)
- Local management following authentication. (Blacklist, Whitelist, CUG groups).
- Encrypted key exchange of symmetrical keys with RSA 102472048 bit
- Encryption of speech: Symmetrical key AES 256 bits.
- New AES session key generated for each call. TMPSYS-Enigma devices negotiate the session key and type of algorithm during connection set-up, as part of transmission-path authentication
- Short authentication time.
- Encrypted Speech quality comparable with GSM standard calls.
- Negligible speech delay during crypto call.
- Encryption Operation as simple as making standard GSM voice calls
- During secure call, NO transmission of plain speech possible (not even by chance or operator error).
- SMS encryption with AES26 bit
- SMS authentication with RSA 2048 bit only
- Customer organized user group for SMS by exchanging Security Cards’ certificates
- No key change for transport or for SMS gateway needed.
Ed.: *1) RSA 1024 bit uses the Hash algorithm RIPEMD 160, RSA 2048 uses Hash algorithm SHA 256 Encrypted SMS only uses Security cards with RSA 2048 bit.
*2) ITSEC: Security evaluation for IT systems
TMPSYS-Enigma T 301 E User Interface
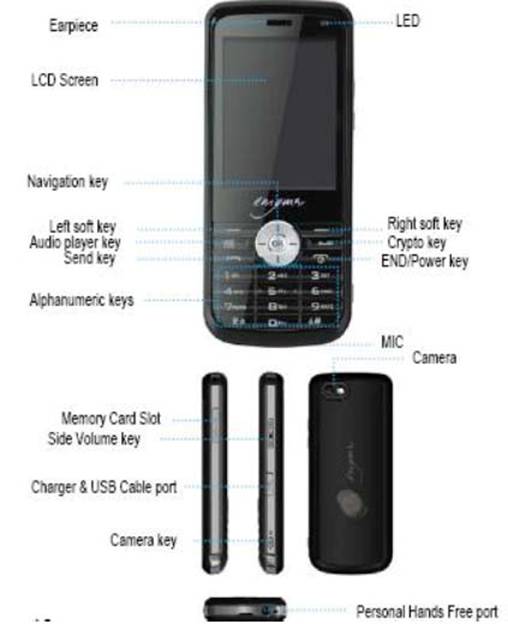
TMPSYS-Enigma T301E Keypad

TMPSYS-Enigma T301E GSM Features
RF Characteristics
GSM Tri-band 900/1800/1900
Physical Parameters
Weight: 94g
Dimension: 116 x 50 x 14.65 mm
Battery
Type: Lithium Ion, Capacity: 930mAh
Organiser
Calendar , Alarm ,World Clock ,Notes , Calculator, Unit Converter Currency Converter, Stopwatch , Crypto management , File Manager , eBook Reader
Multimedia
Camcorder, Image viewer, Video player ,Photo editor ,Audio player ,Sound recorder
Bluetooth
TMPSYS-Enigma T 301 E supports the following Bluetooth profiles: ( only for clear calls ) :Headset , Hands -free ,Dial Up Networking (DUN) ,File Transfer Object Push , A2DP
Camera
CMOS , Resolution: 3.0 Megapixel , Fast Zoom
Data Transmission
Circuit Switched Data ( CSD ) 9,6 kbps.
GPRS Class 12 , max.4 uplink and 4 downlink time slots, active timeslots max. 5, coding scheme 4 (CS 4, 20 kbps. per time slot)
SIM Application Toolkit Class 1, 2, 3
Frequency Allocation
|
GSM-900 |
DCS-1800 |
PCS-1900 |
Power Class |
4 |
1 |
1 |
Max. Output Power |
|33dBm (2Watts) |
30dBm (lWatt) |
30dBm (lWatt) |
Tx Freq. Range |
880.2~914.8 MHz |
1710.2-1784.8 MHz |
1850.2-1909.8 MHz |
Rx Freq. Range |
925.2-959.8 MHz |
1805.2-1879.8 MHz |
1930.2- 1989.8 MHz |
TT/Standby: by nework
Talk Time |
About 4hr 30min |
About 5hr |
About 5hr 30min |
Standby Time |
About 250hr |
About 250hr |
About 250hr |
TT / Standby: by call type
Type of calls |
Talk Time |
Talk Time |
Standby Time |
|
Max power |
Levell2(19dBm) |
|
GSM voice call |
3 hours 30 min |
7 hours 450 |
-600 hours |
Crypto call |
2 hours 30 min |
3 hours |
450 - 600 hours |
Environmental Specification
Normal Temperature: +15°C to +35°C
Operating Temperature: -10°C to +55°C
Charging Temperature: +0°C to +40°C
Normal Humidity Range: 20 to 75%
Storage Temperature: -30°C to +70°C
TMPSYS-Enigma T301E SIM and network requirements for encrypted voice calls
TMPSYS-Enigma T301E uses GSM Circuit Switched Data transmission (CSD). This means creating a connection by setting up an end-to-end communication. The circuit remains open for the duration of the communication and a fixed share of network resources is tied up with no one else is able to make use of them until the connection is closed. The main advantage of circuit-switching is that it enables performance guarantees.
GSM SIM Card subscription must include circuit switched data services under all roaming conditions as follows; Circuit switched data call is required to transfer user data between two mobiles. This means the ability to originate and terminate data calls between itself and another GSM mobile similarly equipped.
The data call required from network is BEARER 26 with following mandatory options:
- Transparent mode.
- V110 intermediate rate.
- UDI. (Unrestricted Digital Information)
- Data Compression not allowed.
With some operators a secondary telephone number (multi - numbering) maybe provided to facilitate this data service (“CSD “).
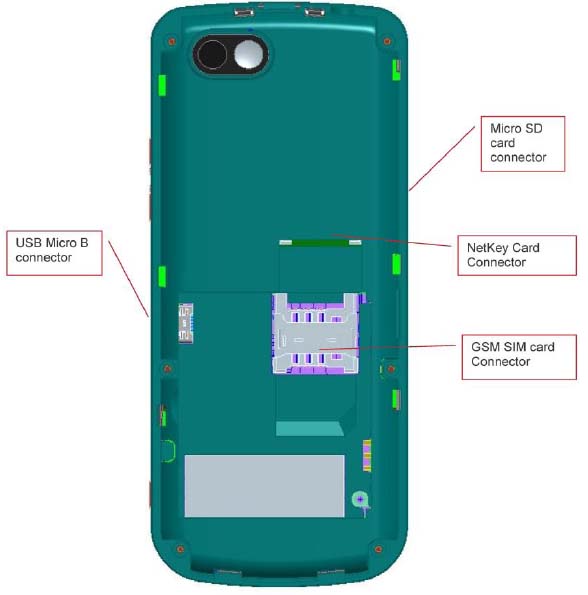
Interface connectors
3.5φ Personal Hands free jack
USB Type Micro 5 pin connector for charging and PC synch and utilities
One GSM SIM card connector under battery lid for GSM access
One Net Key card connector under battery lid for Voice Encryption system
Micro SD card slot: For music, pictures and application data
Overview Security Module Features
Encryption algorithm AES-256bit
Authentication algorithm & key exchange RSA-1024 bit
Authorization algorithms Blacklist/ WhiteList /CUGlist
Hashing algorithms RIPEMD-160
Digital Certificates X509v3
Transportation Data formats V110
Crypto Cards compatibility TeleSec Netkey Cards
Compression Speech Format AMBE-3000
User Interface Features
Local Management,
User Black list,
Communicating partner’s Certificate ID notified in Call records and In Call Screens.
Standard Package
This device and associated firmware is protected by copyright law and international treaties.






















